OpenWrt + WireGuard + Обход блокировок
Доброго времени суток, форумчане.
Настраивал по гайду обход блокировок на роутере и даже написал баш скрипт для личных нужд, который всё это дело автоматически настраивает, но что-то идёт не так.
После настройки на ПК, который подключен по Ethernet к роутеру, всё работает нормально, в том числе открывает заблокированные ресурсы.
При этом девайс, который подключается по Wi-Fi долго пытается открыть любой сайт и выдает ошибку по таймауту. Однако, через какое-то время и на этом девайсе может заработать интернет. Причину и следствие не понял.
Через какое-то время роутер и вовсе может перестать отвечать (ping, ssh), но потом сам заводится =/
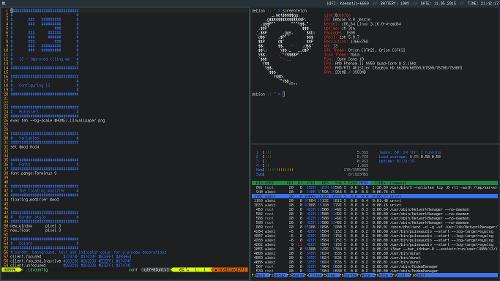
В простое у роутера такая картина:
1 [ 0.0%] Tasks: 19, 0 thr; 1 running
2 [ 0.0%] Load average: 0.27 0.14 0.13
3 [ 0.0%] Uptime: 09:03:14
4 [|| 1.3%]
Mem[||||||||||||||||||||| 111M/248M]
Swp[ 0K/0K]
Во время обновления списка IP адресов ядра нагружаются на секунд 5 и снова всё нормализуется.
Вот скрипт, которым я настраиваю роутер, когда у него дефолтные настройки:
#!/bin/sh
GREEN_COLOR="\033[1;32m"
NO_COLOR="\033[0m"
echo -e "${GREEN_COLOR}Updating list of available packages...${NO_COLOR}"
opkg update
echo
echo
echo -e "${GREEN_COLOR}Installing wireguard package...${NO_COLOR}"
opkg install wireguard
echo
echo
echo -e "${GREEN_COLOR}Configuring wireguard...${NO_COLOR}"
PRIVATE_KEY_OF_CLIENT="HIDDEN"
PUBLIC_KEY_OF_SERVER="HIDDEN"
IP_ADDRESS_OF_SERVER="HIDDEN"
uci set network.wg0=interface
uci set network.wg0.private_key="${PRIVATE_KEY_OF_CLIENT}"
uci add_list network.wg0.addresses="10.0.0.2/32"
uci set network.wg0.listen_port="51820"
uci set network.wg0.proto="wireguard"
uci add network wireguard_wg0
uci set network.@wireguard_wg0[-1].public_key="${PUBLIC_KEY_OF_SERVER}"
uci set network.@wireguard_wg0[-1].allowed_ips="0.0.0.0/0"
uci set network.@wireguard_wg0[-1].route_allowed_ips="0"
uci set network.@wireguard_wg0[-1].endpoint_host="${IP_ADDRESS_OF_SERVER}"
uci set network.@wireguard_wg0[-1].endpoint_port="51820"
uci set network.@wireguard_wg0[-1].persistent_keepalive="25"
uci commit
echo
echo
echo -e "${GREEN_COLOR}Installing ipset and curl packages...${NO_COLOR}"
opkg install ipset curl
echo
echo
echo -e "${GREEN_COLOR}Configuring bypass lock...${NO_COLOR}"
SET_OF_BLOCKED_SUBNETWORKS="blocked-subnetworks"
SET_OF_BLOCKED_IP_ADDRESSES="blocked-ip-addresses"
cat > /etc/init.d/bypass-lock << EOM
#!/bin/sh /etc/rc.common
START=99
start() {
if ! ipset list -n | grep -q "${SET_OF_BLOCKED_SUBNETWORKS}"; then
ipset create "${SET_OF_BLOCKED_SUBNETWORKS}" hash:net \\
family inet \\
hashsize 4194304 \\
maxelem 4194304
fi
if ! ipset list -n | grep -q "${SET_OF_BLOCKED_IP_ADDRESSES}"; then
ipset create "${SET_OF_BLOCKED_IP_ADDRESSES}" hash:net \\
family inet \\
hashsize 4194304 \\
maxelem 4194304
fi
echo "create temporary-${SET_OF_BLOCKED_SUBNETWORKS} hash:net" \\
"family inet" \\
"hashsize 4194304" \\
"maxelem 4194304" \\
> /tmp/blocked-lists
curl https://antifilter.download/list/subnet.lst --silent | while read ip
do
echo "add temporary-${SET_OF_BLOCKED_SUBNETWORKS} \${ip}" >> /tmp/blocked-lists
done
echo "create temporary-${SET_OF_BLOCKED_IP_ADDRESSES} hash:net" \\
"family inet" \\
"hashsize 4194304" \\
"maxelem 4194304" \\
>> /tmp/blocked-lists
curl https://antifilter.download/list/ipsum.lst --silent | while read ip
do
echo "add temporary-${SET_OF_BLOCKED_IP_ADDRESSES} \${ip}" >> /tmp/blocked-lists
done
ipset destroy temporary-${SET_OF_BLOCKED_SUBNETWORKS} -q
ipset destroy temporary-${SET_OF_BLOCKED_IP_ADDRESSES} -q
ipset restore < /tmp/blocked-lists
ipset swap temporary-${SET_OF_BLOCKED_SUBNETWORKS} ${SET_OF_BLOCKED_SUBNETWORKS}
ipset swap temporary-${SET_OF_BLOCKED_IP_ADDRESSES} ${SET_OF_BLOCKED_IP_ADDRESSES}
}
EOM
chmod +x /etc/init.d/bypass-lock
/etc/init.d/bypass-lock enable
/etc/init.d/bypass-lock start
echo "*/5 * * * * /etc/init.d/bypass-lock start" >> /etc/crontabs/root
echo >> /etc/crontabs/root
/etc/init.d/cron enable
/etc/init.d/cron start
echo "99 vpn" >> /etc/iproute2/rt_tables
cat > /etc/hotplug.d/iface/30-add-route << EOM
#!/bin/sh
ip route add table vpn default dev wg0
EOM
uci add network rule
uci set network.@rule[-1].priority="100"
uci set network.@rule[-1].lookup="vpn"
uci set network.@rule[-1].mark="0x1"
uci add firewall zone
uci set firewall.@zone[-1].name="wg"
uci set firewall.@zone[-1].family="ipv4"
uci set firewall.@zone[-1].masq="1"
uci set firewall.@zone[-1].output="ACCEPT"
uci set firewall.@zone[-1].forward="REJECT"
uci set firewall.@zone[-1].input="REJECT"
uci set firewall.@zone[-1].mtu_fix="1"
uci set firewall.@zone[-1].network="wg0"
uci add firewall forwarding
uci set firewall.@forwarding[-1].src="lan"
uci set firewall.@forwarding[-1].dest="wg"
uci add firewall ipset
uci set firewall.@ipset[-1].name="${SET_OF_BLOCKED_SUBNETWORKS}"
uci set firewall.@ipset[-1].storage="hash"
uci set firewall.@ipset[-1].match="dst_net"
uci add firewall ipset
uci set firewall.@ipset[-1].name="${SET_OF_BLOCKED_IP_ADDRESSES}"
uci set firewall.@ipset[-1].storage="hash"
uci set firewall.@ipset[-1].match="dst_net"
uci add firewall rule
uci set firewall.@rule[-1].src="lan"
uci set firewall.@rule[-1].proto="all"
uci set firewall.@rule[-1].ipset="${SET_OF_BLOCKED_SUBNETWORKS}"
uci set firewall.@rule[-1].set_mark="0x1"
uci set firewall.@rule[-1].target="MARK"
uci add firewall rule
uci set firewall.@rule[-1].src="lan"
uci set firewall.@rule[-1].proto="all"
uci set firewall.@rule[-1].ipset="${SET_OF_BLOCKED_IP_ADDRESSES}"
uci set firewall.@rule[-1].set_mark="0x1"
uci set firewall.@rule[-1].target="MARK"
uci commit
echo
echo
echo -e "${GREEN_COLOR}Installing unbound, unbound-control and odhcpd packages...${NO_COLOR}"
opkg install unbound odhcpd unbound-control
echo
echo
echo -e "${GREEN_COLOR}Removing dnsmasq package...${NO_COLOR}"
opkg remove dnsmasq
echo
echo
echo -e "${GREEN_COLOR}Removing default DNS configurations...${NO_COLOR}"
uci delete unbound.@unbound[-1]
uci delete dhcp.@dnsmasq[-1]
uci delete dhcp.wan
uci delete dhcp.lan
uci delete dhcp.odhcpd
uci commit
echo
echo
echo -e "${GREEN_COLOR}Configuring DNS-Over-TLS by Cloudflare...${NO_COLOR}"
cat >> /etc/unbound/unbound_ext.conf << EOM
forward-zone:
name: "."
forward-ssl-upstream: yes
forward-addr: 1.1.1.1@853
forward-addr: 1.0.0.1@853
forward-addr: 2606:4700:4700::1111@853
forward-addr: 2606:4700:4700::1001@853
EOM
uci add unbound unbound
uci set unbound.@unbound[-1].add_local_fqdn="1"
uci set unbound.@unbound[-1].add_wan_fqdn="1"
uci set unbound.@unbound[-1].dhcp_link="odhcpd"
uci set unbound.@unbound[-1].dhcp4_slaac6="1"
uci set unbound.@unbound[-1].domain="lan"
uci set unbound.@unbound[-1].domain_type="static"
uci set unbound.@unbound[-1].listen_port="53"
uci set unbound.@unbound[-1].rebind_protection="1"
uci set unbound.@unbound[-1].unbound_control="1"
uci set dhcp.lan=dhcp
uci set dhcp.lan.dhcpv4="server"
uci set dhcp.lan.dhcpv6="server"
uci set dhcp.lan.interface="lan"
uci set dhcp.lan.leasetime="12h"
uci set dhcp.lan.ra="server"
uci set dhcp.lan.ra_management="1"
uci set dhcp.odhcpd=odhcpd
uci set dhcp.odhcpd.maindhcp="1"
uci set dhcp.odhcpd.leasefile="/var/lib/odhcpd/dhcp.leases"
uci set dhcp.odhcpd.leasetrigger="/usr/lib/unbound/odhcpd.sh"
uci commit
/etc/init.d/unbound enable
/etc/init.d/unbound start
echo
echo
echo -e "${GREEN_COLOR}Restarting network...${NO_COLOR}"
/etc/init.d/network restart
Буду очень благодарен, если кто-то поможет. Сам в сетях не разбираюсь, к сожалению. Если нужны какие-то доп. конфиги, то скину.